integrating IT

ISE Dynamic VLAN assignment
Dynamic VLAN assignment by a RADIUS server (e.g. Cisco ISE) can be useful when you want to assign a specific VLAN to a user or group of users. In order to achieve this the VLANS configured on the switches must be configured with a name, this name must be consistent across multiple switches. However the VLAN number does not necessarily need to be the same across the switches.The scenario in this blog post will simply define 2 VLANS (ADMIN and USERS), members of the AD group Domain Admins will be assigned to a VLAN called ADMIN and members of the AD group Domain Users will be assigned to a VLAN called USERS.
The configuration of ISE in this post only describes the steps in order to configure Dynamic VLAN assignment. Refer to this previous post on how to configure Cisco ISE for 802.1x authentication.
Switch Configuration
Configure the name on the VLANS. These names must match the name specified in the Authorisation Profile on ISE.
ISE Configuration
Authorisation profiles.
- Navigate to Policy > Policy Elements > Results > Authorisation > Authorisation Profiles
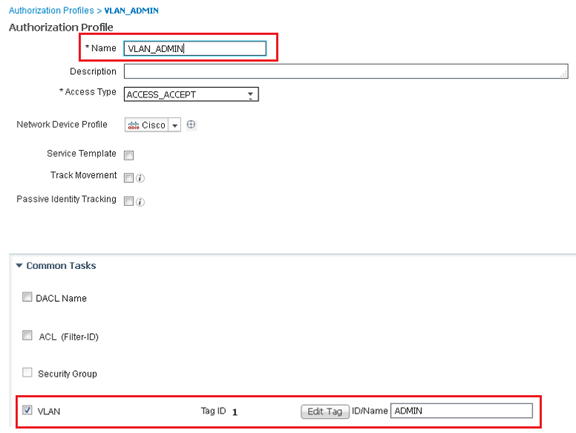
- Create a new Authorisation Profile and name appropriately e.g VLAN_ADMIN
- Under the Common Tasks section, tick VLAN
- Enter the ID/Name of the Admin VLAN as ADMIN
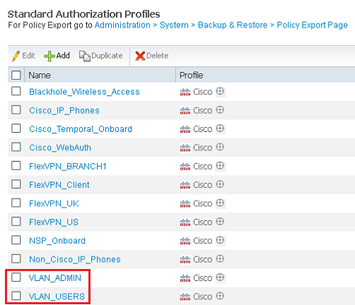
- Repeat the task and create another Authorisation Profile for the Standard Users e.g VLAN_USERS
- Enter the correct ID/Name as USERS
Authorisation Policy
- Navigate to Policy > Policy Set
- Modify an existing Policy Set used for 802.1x
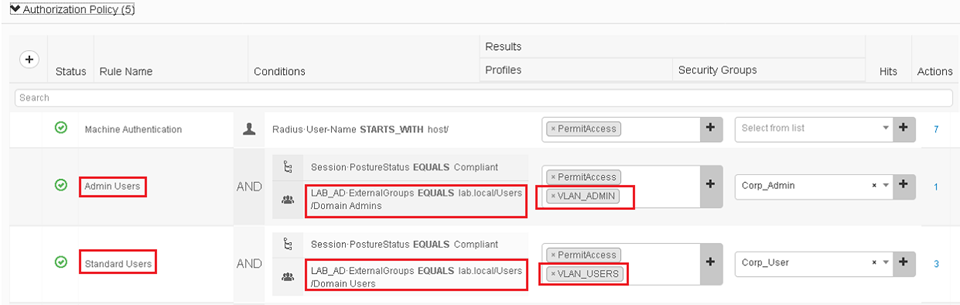
- Ensure there are different Authorization Policy rules, for Admin Users and another for Standard Users
- Assign the VLAN_ADMIN Authorisation Profile to the Admin rule Profiles
- Assign the VLAN_USERS Authorisation Profile to the Standard Users rule Profiles
- Save the policy
Verification
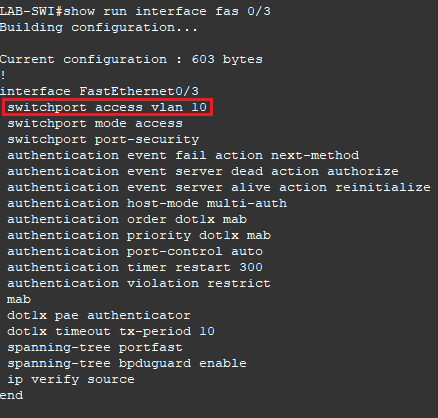
Before logging in as a user, confirm the configuration of the interface the test computer is plugged into. Notice the VLAN is set to VLAN 10.
- Running the command show authentication sessions interface fastethernet 0/3 confirm the computer has a valid IP address in VLAN 10. Notice under Vlan Policy N/A, this means this interface was not dynamically assigned a VLAN.
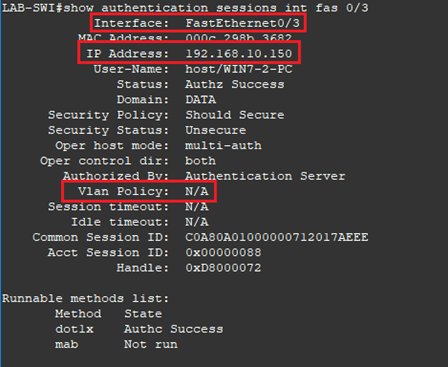
Login as a user that is a member of the AD group Domain Users.
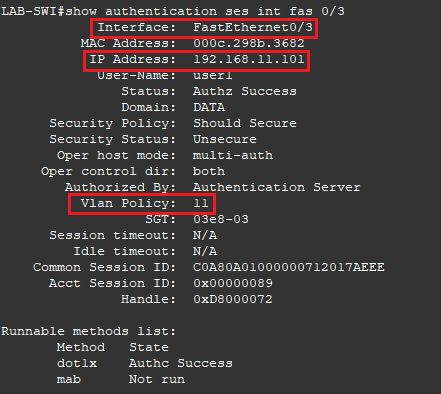
- Run the command show authentication sessions interface fastethernet 0/3
- Compare the output this time with above. Notice the computer now has an IP address from the VLAN 11 DHCP Pool and Vlan Policy = 11, this confirms the computer has dynamically been assigned to VLAN 11.
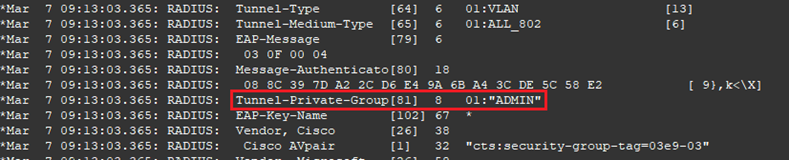
- Run the command debug radius whilst the users is logging on
- You can confirm the VLAN name being returned by successful authorisation by the RADIUS server by the presence of Tunnel-Private-Group .
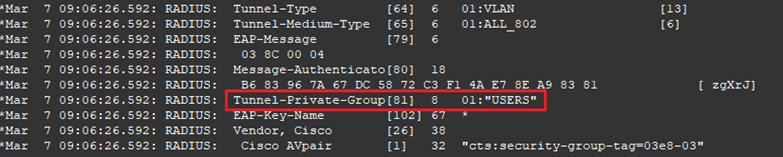
Logoff and log back in as a user in the Domain Admins AD group.
- Compare the output this time with above. Notice the computer now has an IP address from the VLAN 12 DHCP Pool and Vlan Policy = 12
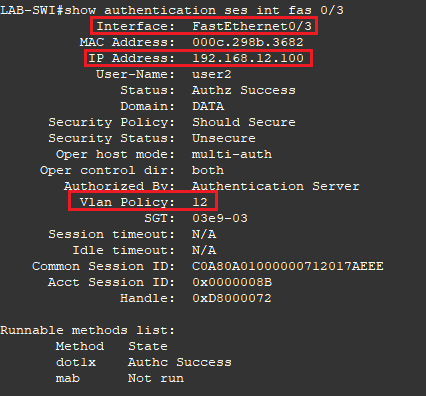
- Running the command debug radius confirms the correct VLAN name ADMIN was sent by the RADIUS server.

Share this:
- Click to share on Twitter (Opens in new window)
- Click to share on Facebook (Opens in new window)
- Click to share on LinkedIn (Opens in new window)
Published by integratingit
View all posts by integratingit
3 thoughts on “ ISE Dynamic VLAN assignment ”
- Pingback: Initial Cisco ISE Configuration – integrating IT
Hi it is cool . What happend if some device has IP fix
If the device has a static IP address and is moved to a different VLAN, the user will not be able to communicate. It will only work if using DHCP.
Leave a comment Cancel reply
This site uses Akismet to reduce spam. Learn how your comment data is processed .

- Already have a WordPress.com account? Log in now.
- Subscribe Subscribed
- Copy shortlink
- Report this content
- View post in Reader
- Manage subscriptions
- Collapse this bar
The Cisco Learning Network

Vasco F Costa asked a question.
Scrambled a file with the configs that I use to have dynamic vlan assigned by my radius server (ISE).
(apologies for such a raw presentation)
- Show more actions
- Enterprise Certifications Community
Vasco F Costa
Just concluded the dynamic vlan authentication with flexconnect.
In the ISE, the config is the same as demonstrated in the pptx file.
I didn't use my ipv6 only network because their not supported in local switch mode:
Cisco Wireless LAN Controller IPv6 Deployment Guide, CUWN Release 8.0 - Cisco
IPV6 and IPv4 are supported on the Flex Connect APs in the Centrally switched mode only. In the Locally switched mode, IPv4 clients work as before with no issues.
wired infrastructure:
For my flexconnect site, I have a l3 switch directly connected to my OSPF area 0.
FLEXRemoto#sh ip route
O E2 192.168.29.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
C 192.168.183.0/24 is directly connected, Vlan803
C 192.168.182.0/24 is directly connected, Vlan802
C 192.168.181.0/24 is directly connected, Vlan801
C 192.168.180.0/24 is directly connected, Vlan800
O E2 192.168.111.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
O E2 192.168.201.0/24 [110/20] via 10.1.1.2, 01:31:36, Vlan1
O E2 192.168.202.0/24 [110/20] via 10.1.1.1, 00:31:00, Vlan1
10.0.0.0/24 is subnetted, 1 subnets
C 10.1.1.0 is directly connected, Vlan1
O E2 192.168.112.0/24 [110/20] via 10.1.1.1, 01:31:36, Vlan1
O E2 192.168.220.0/24 [110/20] via 10.1.1.2, 01:31:36, Vlan1
O E2 192.168.101.0/24 [110/20] via 10.1.1.1, 01:31:36, Vlan1
S* 0.0.0.0/0 [1/0] via 10.1.1.1
O E2 192.168.180.0/23 [110/20] via 10.1.1.1, 00:31:00, Vlan1
switch port where the AP is connected is in trunk mode:
interface FastEthernet0/2
description ->AP Flex
switchport trunk encapsulation dot1q
switchport trunk native vlan 800
switchport mode trunk
spanning-tree portfast
wlan config
- created an wlan "flexdot1x" and assigned to the management interface of the WLC
- for security; it's the same dot1x authentication as I demonstrate in the pptx file.
- advanced tab; clicked on "Allow AAA override"; "Flexconnect Local Switching" and "VLAN based central switching"
- set operation mode as "flexconnect"
- in the "flexconnect" tab; clicked "vlan support" and set native vlan to 800
Flexconnect Group
- created a group
- added the AP to that group
- "ACL mapping" tab -> "AAA VLAN-ACL mapping". Add the same dot1x authenticated vlans (601; 630 and 640). both ingress and egress acl fields were left as "none"
- WLAN VLAN mapping tab; assigned the flexdot1x ssid to vlan 802
Related Questions
Trending articles.
- Cisco Packet Tracer: Software de Simulación para Redes
- 200-301 CCNA Study Materials
- Packet Tracer Labs
- CCIE/CCDE: Book your Lab/Practical Exam
- Basic cisco commands book.pdf
Communities: Recursos Educativos | |
Cisco.com © Copyright 2024 Cisco, Inc. All Rights Reserved. Privacy Statement Terms & Conditions Cookie Policy Trademarks

IMAGES
VIDEO